Answer the following statement(s) true (T) or false (F)
You can find out where various logs are kept on some UNIX and Linux systems by viewing the /etc/syslog.conf or /etc/rsyslog.conf files.
ANSWER: True
You might also like to view...
What is the root of a tree?
What will be an ideal response?
Which of the following statements describes a solution that solves this problem for Cloud Service Consumer A by improving both Cloud A and Cloud B environments?
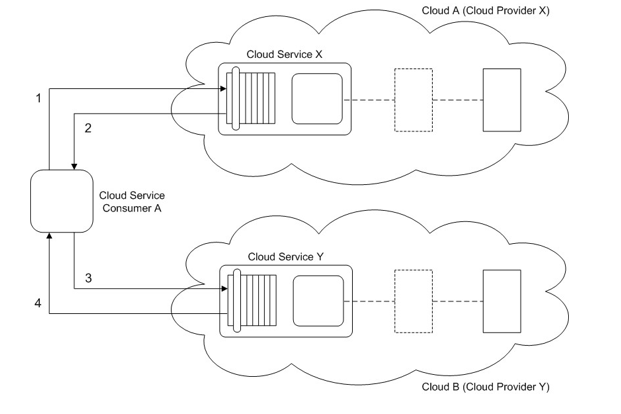
Cloud Service Consumer A accesses Cloud Service X (1) that resides in Cloud A. Cloud Service X processes the request from Cloud Service Consumer A and then sends back a response with the requested data (2). Cloud Service Consumer A then sends a message to Cloud Service Y (3) that resides in Cloud B. The message contains some of the data received from Cloud Service X. After processing the request, Cloud Service Y sends back a response with a success or failure code (4).
Cloud A is a private cloud owned by the same organization that owns Cloud Service Consumer A. Cloud B is a community cloud owned by a group of organizations. The availability rating of Cloud Service X, as indicated in its SLA, is 99.98%. When Cloud Service Consumer A issues a request message to Cloud Service X, it can result in prolonged processes as Cloud Service X attempts to gather the requested data from various data sources. Because Cloud Service X is shared by other cloud service consumers and because the data sources are also shared by other parts of the o
Write a program that inputs a dollar amount to be printed on a check then prints the amount in check-protected format with leading asterisks if necessary. Assume that nine spaces are available for printing an amount.
Computers are frequently employed in check-writing systems such as payroll and accounts-payable applications. Many strange stories circulate regarding weekly paychecks being printed (by mistake) for amounts in excess of $1 million. Weird amounts are printed by computerized check-writing systems, because of human error or machine failure. Systems designers build controls into their systems to prevent such erroneous checks from being issued. Another serious problem is the intentional alteration of a check amount by someone who intends to cash a check fraudulently. To prevent a dollar amount from being altered, most computerized check-writing systems employ a technique called check protection. Checks designed for imprinting by computer contain a fixed number of spaces in which the computer may print an amount. Suppose that a paycheck contains eight blank spaces in which the computer is supposed to print the amount of a weekly paycheck. If the amount is large, then all eight of those spaces will be filled, for example, 1,230.60 (check amount) -------- 12345678 (position numbers) On the other hand, if the amount is less than $1000, then several of the spaces would ordinarily be left blank. For example, 99.87 -------- 12345678 contains three blank spaces. If a check is printed with blank spaces, it’s easier for someone to alter the amount of the check. To prevent a check from being altered, many check-writing systems insert leading asterisks to protect the amount as follows: ***99.87 -------- 12345678
If a text box's TabIndex value is the number 10, what TabIndex value should its identifying label have and why?
What will be an ideal response?