What is another name for static tunnels?
A. private tunnels
B. configured tunnels
C. automatic tunnels
D. self-managed tunnels
Answer: B
You might also like to view...
Every change that is made to a hard disk leaves behind artifacts of that change. Erased data leaves behind file system artifacts even if the data is overwritten on the disk. Electrical charges are altered...metadata is changed. All of these examples are evidence of ____________________ at work.
a. The CSI Effect b. Locard's Exhange Principle c. The Butterfly Effect d. Moore's Law
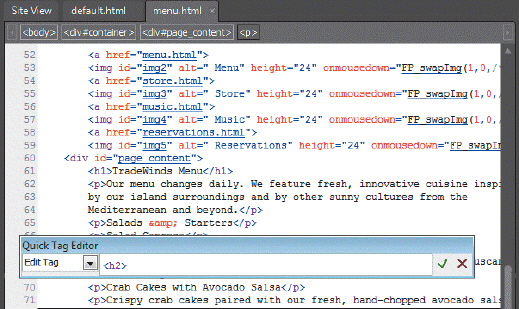 Referring to the figure above, in order to choose "Edit Tag" in the Quick Tag Editor window, what would you do?
Referring to the figure above, in order to choose "Edit Tag" in the Quick Tag Editor window, what would you do?
A. Click on the list arrow shown to the right of "Edit Tag" in the Quick Tag Editor window. B. Choose Insert on the Behaviors tab shown in the right pane. C. Type text in the box that says "Edit Tag" in the Quick Tag Editor window. D. Close the window, choose a section of code, and then open the window again.
Most packet sniffers come bundled with a __________, the tool that takes the sniffed information and figures out what's happening on the network.
A. voltage event recorder B. certifier C. protocol analyzer D. cable tester
Compare one-factor and multiple-factor authentication.
What will be an ideal response?