By defining data members as private, you protect the data and enable access only through the object's methods and properties. This describes the ____ feature.
A. abstraction
B. encapsulation
C. polymorphism
D. inheritance
Answer: B
Computer Science & Information Technology
You might also like to view...
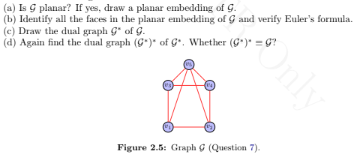
Consider the graph G shown in Figure 2.47 (reproduced in this document as Figure 2.5). Answer the following.
Computer Science & Information Technology
AJAX is an acronym for ____.
A. Asynchronous JavaScript and XML B. Action JavaScript and XML C. Asynchronous Java and XML D. Asymmetric JavaScript and XML
Computer Science & Information Technology
Change the host name of the router to RouterA. List the command sequence required to accomplish this task.
What will be an ideal response?
Computer Science & Information Technology
In a(n) ____ program, each step occurs in the order the programmer determines.
A. procedural B. step-wise C. ordered D. planned
Computer Science & Information Technology