Consider the edge chasing algorithm (without priorities). Give examples to show that it could detect phantom deadlocks.
What will be an ideal response?
Transaction U, V and W perform operations on a data item at each of the servers X, Y and Z in the following order:
U gets data item at Y
V gets data item at X and then blocks at Y.
W gets data item at Z U blocks at Y.
W blocks at X.
V aborts at Y
The table below shows three servers X, Y and Z, the transactions they coordinate, the holders and requesters of their data items and the corresponding wait-for relationships before V aborts:
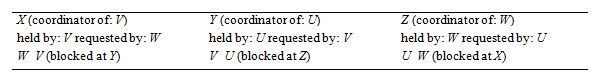
Now consider the probes sent out by the three servers:
At server X: W V (which is blocked at Y); probe
At Y: probe
When V aborts at Y; Y tells X - the coordinator of V, but V has not visited Z, so Z will not be told about the fact that V has aborted!
At Z: probe
You might also like to view...
When a loop statement contains another loop statement it is said to be:
a. nested b. compound c. entangled d. conditional e. none of the above
CGI scripts are known as ________ programs because these programs run on a web server
Fill in the blank(s) with correct word
iReport is a Web site that CNN hosts for capturing user-generated news content.
Answer the following statement true (T) or false (F)
?In addition to joint application development, another popular user-oriented method is _____, which resembles a condensed version of the entire SDLC with users involved every step of the way.
A. ?agile method B. ?sampling C. ?rapid application development D. ?brainstorming