To use an open wireless network without permission is called ________
Fill in the blank(s) with correct word
piggybacking
You might also like to view...
We mentioned that the removemethod calls the private method findEntryIndexto locate the entry to remove. Assuming that the entry is located, what does removeneed to doafter it gets the index of this entry?
What will be an ideal response?
When monitoring your system, you notice an unusually high CPU usage value that is consistently over 90 percent. What is the most likely reason for this concerning CPU state?
A. inadequate disk space B. inadequate memory speed C. inadequate RAM D. inadequate processor speed
Update the class diagrams of Figure 5-29 and Figure 5-31 to include the new objects you identified in Exercise 5-11.
What will be an ideal response?
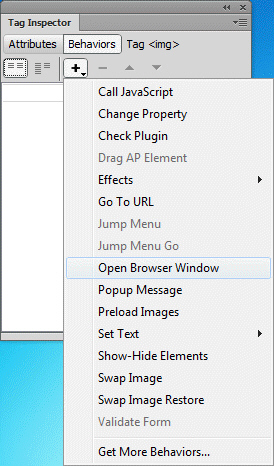 The list of available commands shown in the accompanying figure is the ____.
The list of available commands shown in the accompanying figure is the ____.
A. Behaviors menu B. Actions menu C. Event drop down list D. Special Effects drop down list