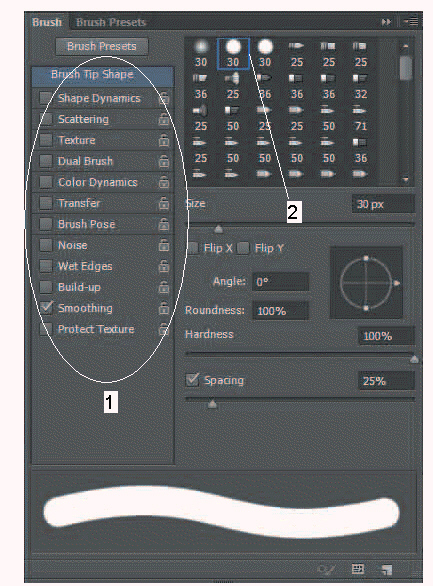
 In the accompanying figure, item 2 is a ____ brush.
In the accompanying figure, item 2 is a ____ brush.
A. hard round
B. soft round
C. hard square
D. soft knife
Answer: A
You might also like to view...
The digital signature approach uses an algorithm that is designed to provide only the _________ function.
A. digital signature B. ElGamal C. DSA D. timestamp
The Financials report shows fixed costs, total costs, baseline costs, variance costs, actual costs, and remaining costs for all tasks.
Answer the following statement true (T) or false (F)
Your company is preparing to upgrade their intrusion detection systems (IDSs) at three locations in the southeast United States. Three vendors have submitted RFP responses that you must evaluate. Each of the three vendor's RFP responses is in-line with the security and other requirements. What should you do to ensure the IDS platform is appropriate for your company?
A. Develop criteria and rate each IDS based on information in the RFP responses. B. Create a lab environment to evaluate each of the three IDSs. C. Benchmark each IDS's capabilities and experiences with similar sized companies. D. Correlate current industry research with the RFP responses to ensure validity.
Do we use lots of codes in our personal and business lives? How many can your class name?
What will be an ideal response?