Malware that changes its binary pattern on specific dates at specific times to avoid detection is known as a (n):
A. armored virus
B. logic bomb
C. polymorphic virus
D. Trojan
Answer: C. polymorphic virus
Computer Science & Information Technology
You might also like to view...
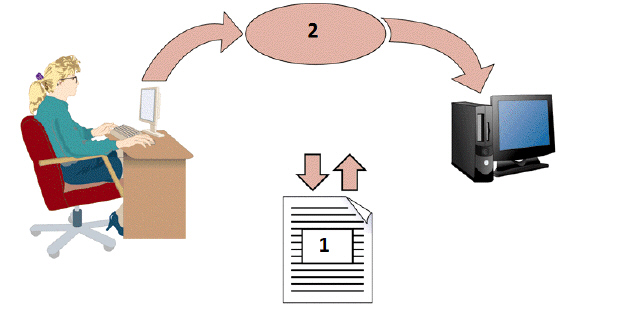 In the figure above, the item numbered 1 indicates the ____.
In the figure above, the item numbered 1 indicates the ____.
A. XML parser B. DTD C. XML prolog D. XML application
Computer Science & Information Technology
Include all of the following when you turn your computer over to a refurbisher except ______ .
A. your data files after backing them up B. the keyboard and mouse C. other peripherals D. your original documentation
Computer Science & Information Technology
The ____________________ bootloader is a very flexible bootloader that can be used to launch just about any system from a computer's hard drive.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Briefly distinguish between OR logic and exclusive OR logic for two inputs.
What will be an ideal response?
Computer Science & Information Technology