MySQL ____________ can speed up query execution as well as protect against SQL injection attacks.
a. query hints
b. stored procedures
c. triggers
d. prepared statements
d. prepared statements
You might also like to view...
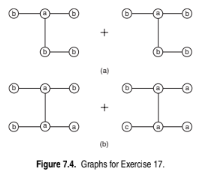
Draw all the candidate subgraphs obtained by joining the pair of graphs shown in Figure 7.4. Assume the edge-growing method is used to expand the subgraphs.
What is the purpose of the Internet layer in the TCP/IP protocol suite?
What will be an ideal response?
Match each term with the correct statement below.
A. Used to return a value back to the calling method B. The first line of a method C. Data components of a class D. The combination of the method name and the number, types, and order of arguments E. Variables in the method declaration that accept the values from the actual parameters F. Are called class methods G. Variables you declare within a class, but outside of any method H. Included within the method declaration parentheses I. An application or a class that instantiates objects of another prewritten class J. Encapsulating method details in a class K. Unreachable statements that can never execute L. Classes that can be used as the basis for any other class M. Method that retrieves a value N. Method that sets or changes field values O. Allocates memory for an object
What can you use to scramble information so that it cannot be read unless the user possesses a key? (516559)
What will be an ideal response?