A __________________ will attempt to determine the information that it requires by probing the target and trying to solicit a response that will allow it to determine some detail about the software running on the host and its configuration.
Fill in the blank(s) with the appropriate word(s).
vulnerability scanning tool
Computer Science & Information Technology
You might also like to view...
Briefly explain the process of adding a header and footer to a Microsoft Word document.?
What will be an ideal response?
Computer Science & Information Technology
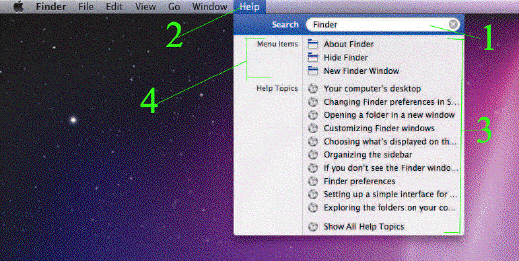 In the accompanying figure, Item 3 points to the ____.
In the accompanying figure, Item 3 points to the ____.
A. Help menu B. Search field C. Search results list D. Menu items section
Computer Science & Information Technology
Access opens in ____ view.
A. Design B. Datasheet C. Layout D. Backstage
Computer Science & Information Technology
Choose the correct sentence.?
A. ?Today Karen read the news article, "What's in It for Me," and three chapters of the novel, The Jury. B. ?Today Karen read the news article, What's In It for Me, and three chapters of the novel, The Jury. C. ?Today Karen read the news article, "What's In It for Me," and three chapters of the novel, "The Jury."
Computer Science & Information Technology