Which type of DoS attack targets an individual client and spoofs a deauthentication frame from the WAP to the victim?
a. Authentication flood attack
b. Deauthentication flood attack
c. Network jamming attack
d. Equipment destruction attack
ANS: B
You might also like to view...
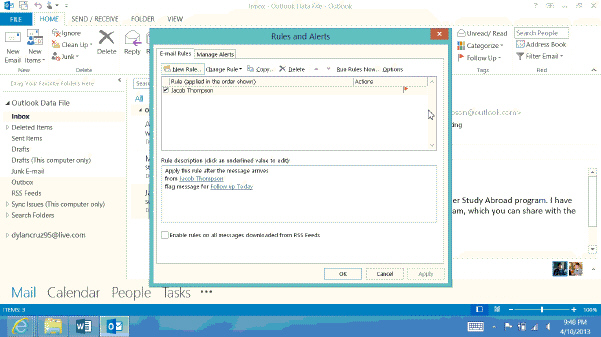 If you want to apply rules to email messages that you already received, you use the ____, as shown in the accompanying figure.
If you want to apply rules to email messages that you already received, you use the ____, as shown in the accompanying figure.
A. Apply Rules dialog box B. Rules and Alerts dialog box C. Email Messages dialog box D. Received Messages dialog box
A ________ provides data in an easy-to-read format suitable for printing
A) report B) query C) form D) table
Like Word, Excel, and PowerPoint, a new database opens when you start Access.
Answer the following statement true (T) or false (F)
Customized software can enable an organization to shape a specialized business strategy to achieve a unique market niche or soar ahead of the competition.
Answer the following statement true (T) or false (F)