What are the steps involved in a buffer overflow exploit?
What will be an ideal response?
First the hacker searches for a chance to overflow the buffer. Next the hacker determines the memory assigned to the variable. Finally, the hacker specifies a value greater than the maximum capacity of the variable and either the stack becomes corrupted, causing the computer to crash, or the instruction pointer directs the program to the memory space that is specified by the hacker.
You might also like to view...
The modulus operator cannot be used to divide numbers that contain a decimal place.
Answer the following statement true (T) or false (F)
Why is it important to examine a spreadsheet before importing it into Access? p.000
What will be an ideal response?
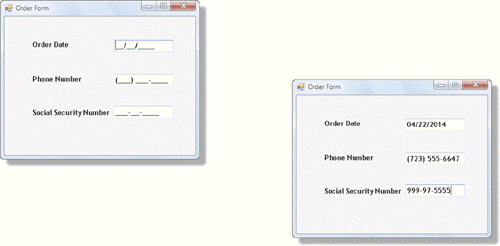 As illustrated in the accompanying figure, the term ____________________ refers to a predefined layout for the data a user must enter.
As illustrated in the accompanying figure, the term ____________________ refers to a predefined layout for the data a user must enter.
Fill in the blank(s) with the appropriate word(s).
Desktop computers have two types of viewports: a visual viewport and a layout viewport.?
Answer the following statement true (T) or false (F)