A customer has several mobile device users who have a habit of misplacing their devices during the workday.
Which of the following security methods will most benefit these users?
A. OS updates
B. Firewalls
C. Trusted sources
D. Locator applications
Answer: D
Computer Science & Information Technology
You might also like to view...
When you delete a file in Windows 8.1, it is actually stored in the ________ where you have a second chance to decide if you still need the file
Fill in the blank(s) with correct word
Computer Science & Information Technology
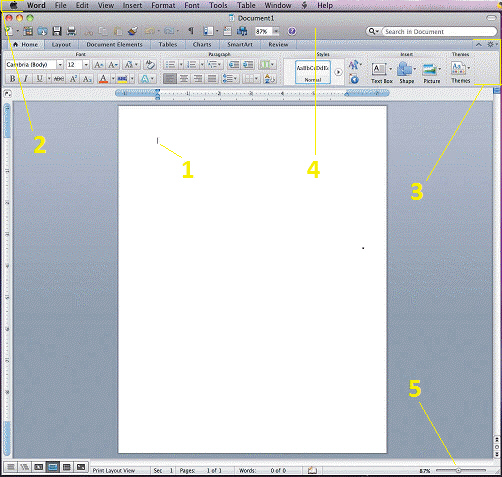 In the accompanying figure, Item 3 points to the ____.
In the accompanying figure, Item 3 points to the ____.
A. status bar B. title bar C. menu bar D. ribbon
Computer Science & Information Technology
By default, field values in an external text file that are being inserted in a table are separated by the ____ keyboard characte
a. comma b. semicolon c. space d. tab
Computer Science & Information Technology
The standard header file for the abs(x)function is ____.
A.
Computer Science & Information Technology