The _________ cloud deployment model is the most secure option.
A. public B. private
C. community D. hybrid
B. private
You might also like to view...
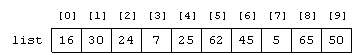 Why can't a binary search be used on the list as it appears in the accompanying figure?
Why can't a binary search be used on the list as it appears in the accompanying figure?
A. Because the list is too big B. Because the list is not sorted C. Because it is a list of integers D. A binary search can be used on the list
In 1854, George Boole, the first Professor of Mathematics at Queen's College in Cork, Ireland, published a book titled An Investigation into the Laws of Thought, on Which are Founded the Mathematical Theories of Logic and Probabilities.
Answer the following statement true (T) or false (F)
A code generator allows users to modify a report easily at any stage of the design process.
Answer the following statement true (T) or false (F)
The _____File Transfer Protocol (FTP)client software is available for several OS platforms, including Windows, Mac, and Linux.?
A. ?SmartFile B. ?FileVector C. ?RealFile D. ?FileZilla