What three things can authentication for IPsec be based upon?
What will be an ideal response?
The authentication for IPsec can be based on:
* Pre-shared key-This is a password that needs to be configured on both the VPN client and the remote access server. A pre-shared key is relatively easy to implement, but, since a single password is shared by all clients and the remote access server, this is not very secure.
* Certificates-If the VPN client and the remote access server have both been configured with certificates that are trusted, then certificate authentication can be used. This is more secure than a pre-shared key, but it can be awkward to deploy certificates to all of the VPN clients.
* Kerberos-Windows-based networks use Kerberos to authenticate users and computers. This same protocol can be used by IPsec. Using IPsec is only possible if the VPN client computer and the remote access server are members of the same Active Directory forest.
You might also like to view...
To help blog visitors find a blog post on a specific topic, which of the following should be added to a post?
a. A label b. A blog directory c. A topic category d. A subscription link
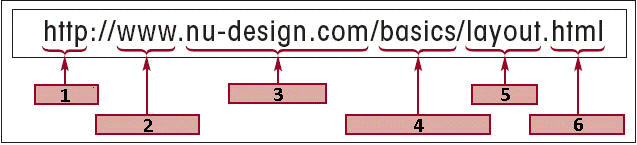 In the URL shown in the accompanying figure, http is the ____.
In the URL shown in the accompanying figure, http is the ____.
A. protocol B. machine name C. domain name D. filename
You can use the ____ tool to select the individual anchor points and line segments of vector graphics.
A. Direct Selection B. Link Selection C. Bound Selection D. Object Selection
What is a term used in typography that is defined in terms of the point size of a particular font?
a. Toast b. View c. Em d. Px