In Internet Protocol Security (IPsec) ____________________ mode, the entire IP packet is encrypted and then placed into an IPsec endpoint where it is encapsulated inside another IP packet.
Fill in the blank(s) with the appropriate word(s).
tunnel
Computer Science & Information Technology
You might also like to view...
The CPU is composed of the control unit and the ________
Fill in the blank(s) with correct word
Computer Science & Information Technology
To select multiple symbols, press and hold ____ and then click the symbols.
A. [Esc] B. [Shift] C. [Alt] D. [F8]
Computer Science & Information Technology
You can add three-dimensional effects to an WordArt object
Indicate whether the statement is true or false
Computer Science & Information Technology
FIGURE 1-1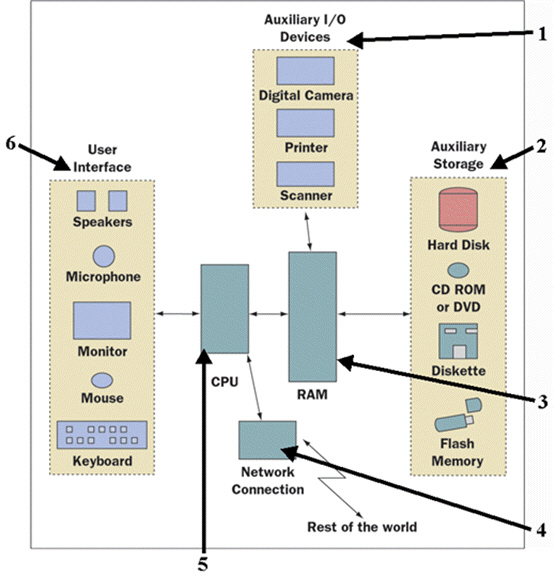 In Figure 1-1 above, which number subsystem is used for long-term storage of data and programs?
In Figure 1-1 above, which number subsystem is used for long-term storage of data and programs?
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology