Roger’s company is trying to increase the level of security for its network. Roger is researching ways to increase the security by making passwords more complex.
?
What can Roger change in Windows to require more complex passwords?
A. Group Policy
B. Organizational unit
C. Password Policy
D. Access control List
Answer: C
You might also like to view...
For the graph G shown in Figure 10.1, compute the following using the weight matrix–based approach:
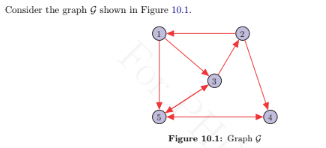
(a) Shifted version of a graph signal
f = [2,?3,1,8, 0]T.
(b) Total variations of all the eigenvectors.
(c) GFT coefficients ordered from low to high frequency.
A query that displays an input box that asks for criteria each time the query is run is called a(n) _________ query
Fill in the blank(s) with correct word
American courts have ruled that the program that removes copy protection from a DVD violates the ____.
A. DMCA B. NET Act C. Net Neutrality Act D. USA PATRIOT Act
Microsoft Windows, used on many personal computers, and the MAC OS, used exclusively on Macintosh computers, are referred to as ____.
A. graphical user interfaces B. programming languages C. operating environments D. device drivers