A user is attempting to access a shared file locally on their workstation. The file has Full control NTFS permissions assigned, and Read permissions at the share level. What is the effective permissions for the user on the file?
A. Full control
B. Modify
C. Read
D. Read and write
Answer: A
Computer Science & Information Technology
You might also like to view...
Explain the differences between fail-soft and fail-safe.
What will be an ideal response?
Computer Science & Information Technology
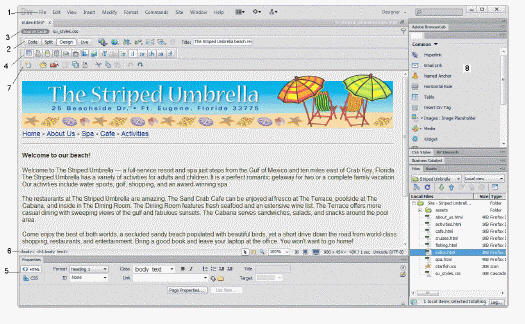 Item ____ in the accompanying figure is the Insert panel.
Item ____ in the accompanying figure is the Insert panel.
A. 2 B. 5 C. 6 D. 8
Computer Science & Information Technology
Most of the connections that make up the high-speed backbone of the Internet use technologies designed at least 20 years ago to support telephone calls.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
What are two valid methods to deploy an OVF template which consists of two or more VMs? (Choose two)
a. Deploy on the VMware vSphere Hypervisor b. Deploy on a vSphere DRS enabled cluster c. Deploy on a vSphere HA enabled cluster d. Deploy on the standalone host connected to vCenter Server
Computer Science & Information Technology