An aggressive, intentional act carried out by a group or individual, using electronic forms of contact, repeatedly and over time against a victim who cannot easily defend him- or herself is known as ________
Fill in the blank(s) with the appropriate word(s).
Answer: cyberbullying
You might also like to view...
As your desktop background, you must use an approved Microsoft image
Indicate whether the statement is true or false
Where is the Show Formulas command found?
A) Formula Auditing group on the Formulas tab B) Formula Auditing group on the Data tab C) Formula Auditing group on the Developer tab D) Formula Auditing group on the Review tab
 As shown in the accompanying figure, ____ the physical equipment associated with a computer.
As shown in the accompanying figure, ____ the physical equipment associated with a computer.
A. computer hardware is B. computer software is C. computer programs are D. computer cables are
?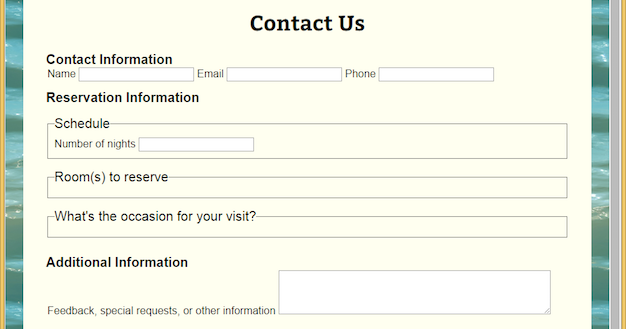
A. input B. textarea C. fieldset D. field