Based on the limited information provided in the depicted scenarios, list the types of attacks that could potentially be carried out if any of the programs outside of the cloud were malicious. Provide a brief explanation justifying the threat of each proposed attack.
The diagram below illustrates the interaction between two cloud service consumers (A and B) and two virtual servers (A and B) hosted on a cloud.
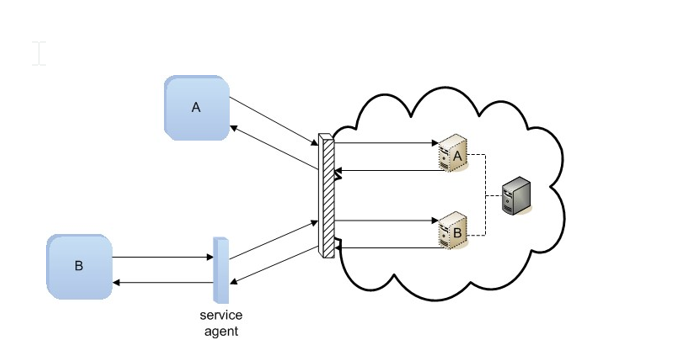
Cloud Service Consumer A could launch a denial of service attack on Virtual Server A by generating increased loads that could compromise the underlying physical server and, as a result, could further compromise Virtual Server B.
Cloud Service Consumer B could launch its own denial of service attack, as described above, thereby compromising Virtual Server B, the underlying physical server, and potentially also Virtual Server A.
The service agent could be designed to launch a malicious intermediary attack by intercepting messages or data received by cloud service consumer B and augmenting the data in a manner that could be harmful to Virtual Server B.
Cloud Service Consumer A could attempt to take advantage of the fact that it shares an overlapping trust boundary with Cloud Service Consumer B.
Similarly, Cloud Service Consumer B can attempt to abuse its overlapping trust boundary with Cloud Service Consumer A.
You might also like to view...
As you work, the History panel logs each command that is performed as a new ____________________.
Fill in the blank(s) with the appropriate word(s).
What are the four guidelines that system analyst follow to design a good form, a preprinted or duplicated paper that requires people to fill in responses in a standardized way.
What will be an ideal response?
Which of the following will correctly insert a background sound that will play one time?
A)
The ROLLBACK command reverses changes made to a table's structure.
Answer the following statement true (T) or false (F)