Describe forged deauthentication.
What will be an ideal response?
The attacker monitors transmissions to identify target stations. When a data frame or association response frame is captured, the attacker sends a spoofed deauthentication frame that contains the AP's MAC address. To prevent reconnection, the attacker continues to send deauthentication frames for the duration of the attack.
You might also like to view...
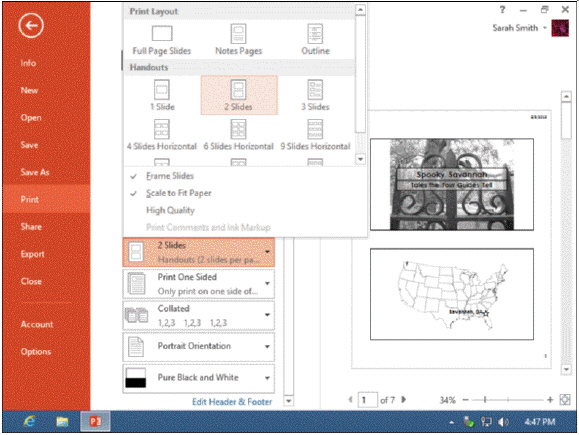 Referring to the accompanying figure, which of the following layouts prints blank lines to the right of each slide?
Referring to the accompanying figure, which of the following layouts prints blank lines to the right of each slide?
A. 3 slides B. 2 slides C. 4 slides D. 6 slides
Double-clicking the Hand tool on the Tools panel also fits the image on the screen.
Answer the following statement true (T) or false (F)
Which threading model can threads created using the clone system call implement?
What will be an ideal response?
You can enable disk and volume quotas from File Explorer or from the FSRMconsole. Enabling quotas from __________ permits you to set different quotas for different users
Fill in the blank(s) with correct word