?
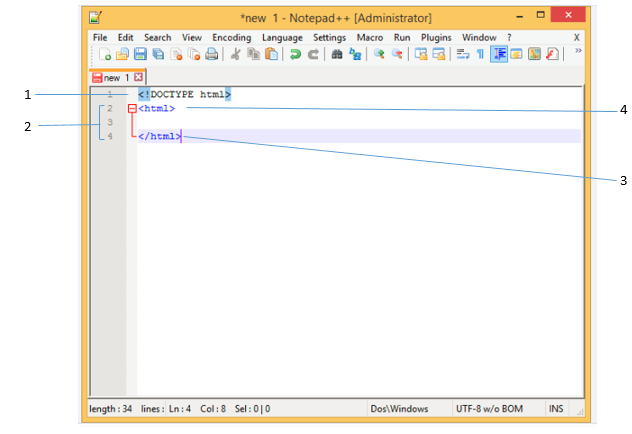
In the figure above, item #3 shows a(n) ____ tag.
A. comment
B. closing
C. preview
D. opening
Answer: B
Computer Science & Information Technology
You might also like to view...
A(n) ________ is an attack in which multiple systems are used to flood servers or network devices or links with traffic in an attempt to overwhelm its available resources, making it unavailable to respond to legitimate users.
A) DDoS B) DoS C) ODC D) SAL
Computer Science & Information Technology
You cannot make adjustments to your report under the Layout View
Indicate whether the statement is true or false
Computer Science & Information Technology
To include a header file in a program, you use the preprocessor command ____.
A. pragma B. fetch C. pull D. include
Computer Science & Information Technology
The conditional expression in the while statement is enclosed within ____ following the keyword while.
A. slashes B. parentheses C. asterisks D. dashes
Computer Science & Information Technology