Posting information to the Internet using anonymous email accounts or screen names makes it impossible to identify a libeler.
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
Which of the following is used to issue digital certificates?
A) Certificate authority B) Registration authority C) PKI D) Certificate revocation list
Computer Science & Information Technology
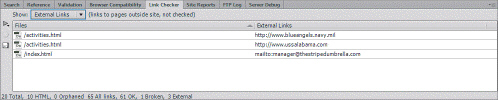 The accompanying figure shows the ____.
The accompanying figure shows the ____.
A. Link diagnostic tool B. Link Checker C. File map D. Link map
Computer Science & Information Technology
Expressions within ________ are calculated first in formulas containing several math operators
Fill in the blank(s) with correct word
Computer Science & Information Technology
____ can be extremely distressing for victims, can take years to straighten out, and can be very expensive.
A. Spams B. Identity theft C. Remote access D. Software theft
Computer Science & Information Technology