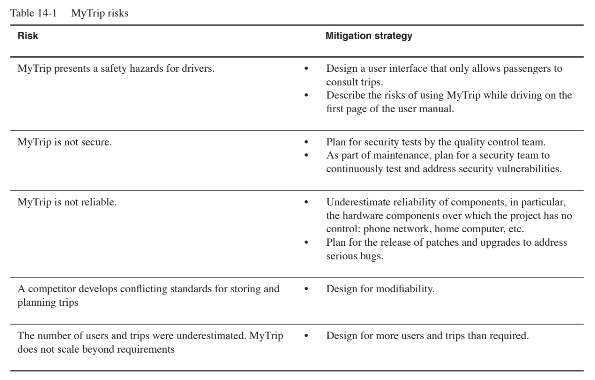
Identify, prioritize, and plan for the top five risks related to the system design of MyTrip presented in Chapter 6, System Design: Decomposing the System.
What will be an ideal response?
Note to the instructor: Again, the risks provided by the students need not be realistic. They do need, however, to be
risks. The goal of the exercise is to make the students think about what could go wrong and to check their
understanding of the risk concept. Table 14-1 is an example solution of risks and corresponding mitigation strategies.
The risks are ordered by priority (most important first).
You might also like to view...
How many bits are in a byte?
a) 4 b) 8 c) 16 d) 256
PowerPoint's ________ make it possible to move back and forth between slides and go to the end of a presentation
A) plotting aids B) navigation tools C) locator links D) transition effects
The ____________________ publishing option uploads all of the site pages to a folder on your computer or on a network folder to which you have access.
Fill in the blank(s) with the appropriate word(s).
Which of the following system and security tasks provides a summary of information related to your computer?
a. Action Center b. System c. Administrative Tools d. Windows Log