Phishing attacks are carried out solely through email
Indicate whether the statement is true or false
False - Fake websites are also used for phishing attacks.
You might also like to view...
Which of the following statements is false?
a. Each class declaration that begins with the access modifier private must be stored in a file that has the same name as the class and ends with the .java filename extension. b. Every class declaration contains keyword class followed immediately by the class’s name. c. Class, method and variable names are identifiers. d. An object has attributes that are implemented as instance variables and carried with it throughout its lifetime.
Both Hyper-V on Windows Server and Client Hyper-V on Windows 10 offer the same core functionality that allows you to run virtual machines.
Answer the following statement true (T) or false (F)
Case-based Critical Thinking QuestionsCase 14-2Urma has begun to apply the basic information that you have given her about schemas, and she to understand a schema with and without qualified XML Schema object names.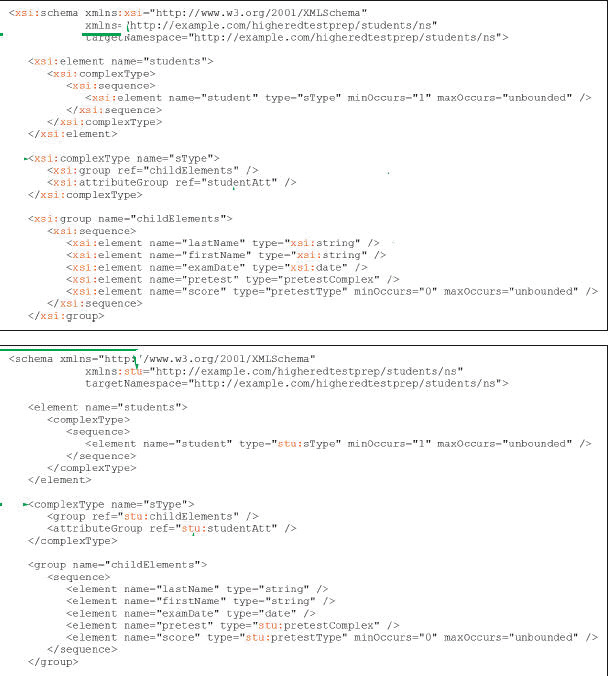 In the example code,
In the example code,
A. xsi B. attributeGroup C. ref D. studentAtt
A(n) ________ function uses a set of reference cells arranged in columns
Fill in the blank(s) with correct word