Second normalization takes care of:
a. the insertion anomaly
b. the update anomaly
c. the deletion anomaly
d. the schema
b. the update anomaly
You might also like to view...
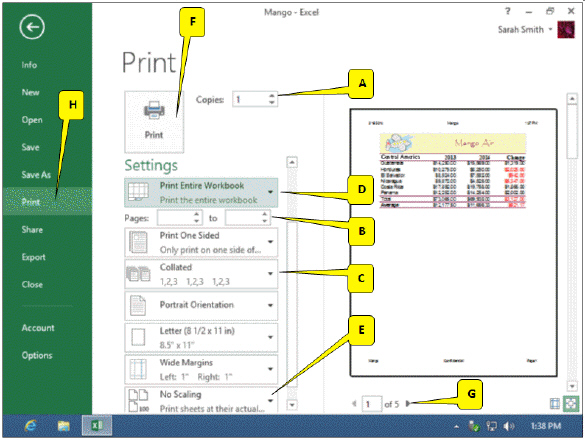 In the accompanying figure, which callout points to the option that allows you to change the default printing option, which prints the active worksheet?
In the accompanying figure, which callout points to the option that allows you to change the default printing option, which prints the active worksheet?
A. A B. B C. C D. D
A(n) ________ control is a control that does not have a source of data such as the title of the form
A) unbound B) bound C) calculated D) text box
Users tend to choose passwords that are easy to remember. Passwords can often be broken by repeated trials. Users tend to write their passwords down. They tend to choose passwords that can be deduced by someone who knows the user (telephone numbers, name of a close friend, something about the user such as a hobby, and the like). Also, users tend to use the same password for many different systems.
What will be an ideal response?
One way to open a found file is to ____ it.
A. double-click B. click C. hover over D. left-click