Which of the following is another term for the layered security model?
A. extreme defenses
B. defense-in-depth
C. security-immersion
D. total-security-strategy
Answer: B
You might also like to view...
In a producer/consumer relationship with a single cell of shared memory, which of the following is true?
a. The consumer must run first. b. The producer must run first. c. The producer must run first or the consumer will have to wait. d. The consumer must run first or the producer will have to wait.
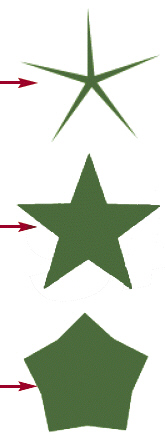 The middle star in the accompanying figure has a point size of ____.
The middle star in the accompanying figure has a point size of ____.
A. 0 B. 0.5 C. 1 D. 5
Which Cisco IOS statement would correctly match only the IP range from 172.30.64.0 through 172.30.127.255?
A) access-list 1 permit 172.30.64.0 0.0.63.255 B) access-list 1 permit 172.30.0.0 0.0.63.255 C) access-list 1 permit 172.30.64.0 0.0.127.255 D) access-list 1 permit 172.30.0.0 0.0.127.255
You can traverse a 2-3 tree in sorted order by performing the analogue of a(n) _______ traversal on a binary tree.
a. pre-order b. post-order c. tri-order d. in-order