A technology that provides information about your computer usage to remote third parties is called
a. a computer hard drive.
b. a firewall.
c. a cookie.
d. a sensor.
C
You might also like to view...
The following information regarding a dependent variable y and an independent variable x is provided:
?x = 90?(y - 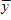
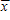
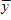
If property covered by a valued policy is totally destroyed, the ________.
A. insured can recover only the fair market value of the property B. insured can recover the fair market value of the property at the time it was destroyed, up to the limits stated in the policy C. insured can recover the face amount of the policy regardless of the fair market value of the property D. insured can recover the face amount of the policy only if it does not exceed the fair market value of the property
Ashe Corporation has two manufacturing departments--Machining and Customizing. The company used the following data at the beginning of the year to calculate predetermined overhead rates: ?Machining CustomizingTotalEstimated total machine-hours (MHs) 1,000 4,000 5,000Estimated total fixed manufacturing overhead cost$4,700$9,200$13,900Estimated variable manufacturing overhead cost per MH$1.10$2.60 During the most recent month, the company started and completed two jobs--Job B and Job K. There were no beginning inventories. Data concerning those two jobs follow: Job BJob KMachining machine-hours 700 300Customizing machine-hours 1,600 2,400 Assume that the company uses departmental predetermined overhead rates with machine-hours as the allocation base in both production
departments. The manufacturing overhead applied to Job K is closest to: A. $1,740 B. $13,716 C. $13,500 D. $11,760
_____ describes interactions between organizational units on the same hierarchical level.
A. Peripheral communication B. Vertical communication C. Horizontal communication D. External communication