The exposure of an asset supported by a strong control to a threat of annual occurrence is 3. The impact of the threat on the asset is very high. Using the NIST framework, the risk equals
2
1
5
4
Answer: 1
Computer Science & Information Technology
You might also like to view...
Which command executes the Java class file Welcome.class?
a. java welcome b. java Welcome.class c. java Welcome d. run Welcome.class
Computer Science & Information Technology
Describe what a shared subclass represents and how does this concept relate to multiple inheritance.
What will be an ideal response?
Computer Science & Information Technology
Instead of multiplying samples by a multiplier (like 2 or 0.5), try adding a value to them.
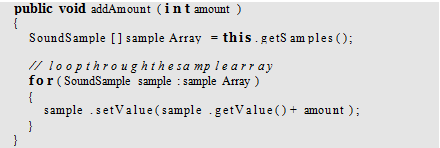
Computer Science & Information Technology
A user ____ is what the user sees and interacts with while an application is running.
A. service B. profile C. splash D. interface
Computer Science & Information Technology