An attacker types more data in a field than the programmer expected. This is a(n) ________ attack
A. buffer overflow
B. denial-of-service
C. directory traversal
D. XSS
A. buffer overflow
You might also like to view...
Transmitting a block of data, waiting for a positive acknowledgement message, and then proceeding with the next block transmission, is known as
a. stop-and-wait ARQ b. go-back-N continuous ARQ c. SDLC d. PPP
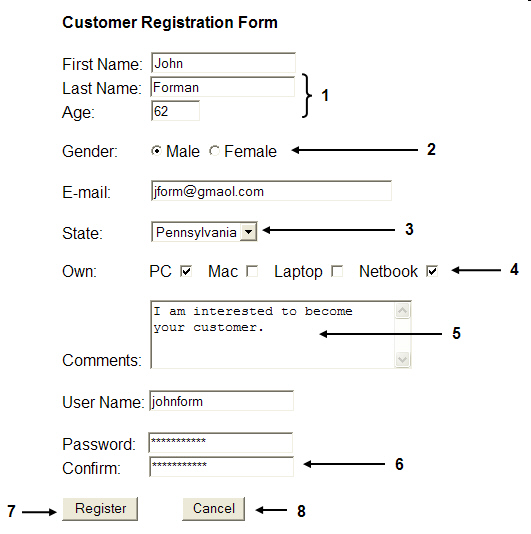 The ____ attribute sets the length of the text boxes marked 1 in the accompanying figure.
The ____ attribute sets the length of the text boxes marked 1 in the accompanying figure.
A. length B. size C. width D. dimension
Which of the following provides the BEST environment for prototyping?
A. a public cloud B. a virtualized environment C. a private cloud D. a hybrid cloud
All of the following tests of controls will provide evidence about the physical security of the computer center except
A. review of fire marshal records B. review of the test of the backup power supply C. verification of the second site backup location D. observation of procedures surrounding visitor access to the computer center