________ is any computer program designed to infiltrate or damage an infected computer
Fill in the blank(s) with correct word
Malware
Computer Science & Information Technology
You might also like to view...
The ________ is used to input voice commands or text
Fill in the blank(s) with correct word
Computer Science & Information Technology
When the ____ button is not selected, the Camera app captures a photo.
A. Camera B. Quick capture C. Photo capture D. Video
Computer Science & Information Technology
?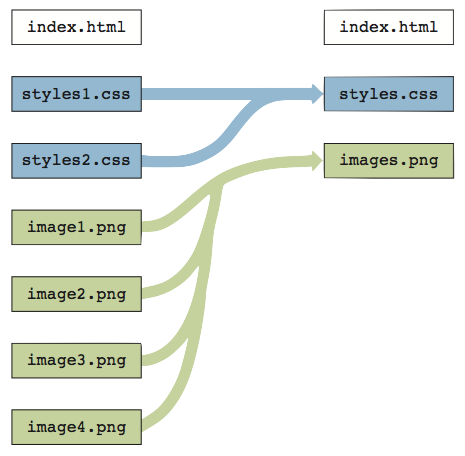
A. 3 B. 1 C. 7 D. 0
Computer Science & Information Technology
Which of the following security policies can be implemented to prevent removable media from automatically launching potentially harmful programs?
A. Disable AutoPlay. B. Disable AutoRun. C. Disable the Guest account D. Enable screen lock.
Computer Science & Information Technology