Which of the following type of hackers hacks into systems to cause harm or steal data?
a. White hat
b. Gray hat
c. Green hat
d. Black hat
ANS: D
You might also like to view...
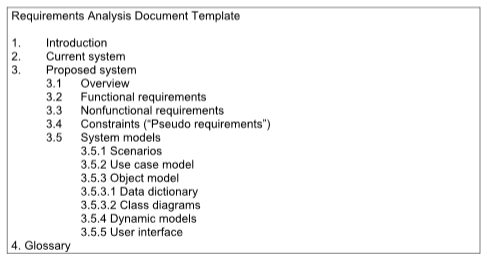
Reverse engineer the requirements of the Heathrow airport luggage system and communicate your results using the Requirements Analysis Document template presented in the lecture.
Questions to ask:
• How are the bags stored after passengers have checked, but before they
enter the plane?
• How are the bags retrieved from the storage area?
• What about existing luggage systems (“legacy systems”)?
• Scalability: How many users should the new luggage system support? How can
this be tested before deployment?
• Throughput: How many suit cases/hour need to be supported?
When project managers discuss slack, they are generally referring to free slack.
Answer the following statement true (T) or false (F)
________ graphics are created using geometrical formulas and can be easily edited and layered
Fill in the blank(s) with correct word
Because of ____, the value assigned to the variable on the left side of the assignment operator is forced into the data type of the variable to which it’s assigned.
a. right-to-left associability b. left-to-right associability c. coercion d. operator precedence