When a presentation is viewed as a slide show, the entire slide fills the screen
Indicate whether the statement is true or false
TRUE
You might also like to view...
The original association rule mining framework considers only presence of items together in the same transaction. There are situations in which itemsets that are infrequent may also be informative. For instance, the itemset TV, DVD, ¬ VCR suggests that many customers who buy TVs and DVDs do not buy VCRs. In this problem, you are asked to extend the association rule framework to negative itemsets (i.e., itemsets that contain both presence and absence of items). We will use the negation symbol (¬) to refer to absence of items.
(a) A na ??ve way for deriving negative itemsets is to extend each transaction
to include absence of items as shown in Table 7.17.
i. Suppose the transaction database contains 1000 distinct items.
What is the total number of positive itemsets that can be generated from these items? (Note: A positive itemset does not contain
any negated items).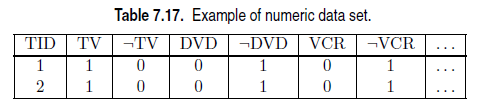
ii. What is the maximum number of frequent itemsets that can be
generated from these transactions? (Assume that a frequent item-
set may contain positive, negative, or both types of itemsiii. Explain why such a na ??ve method of extending each transaction
with negative items is not practical for deriving negative itemsets.
What clause of the ISO 12207 standard outlines the measurement process?
A. 6.3.4 B. 6.3.5 C. 6.3.6 D. 6.3.7
A file stream, fStr, is open and attached to physical file.txt. To reset this file stream so that the file can be read again starting at the first line requires
a. “File stream fStr, reset yourself to the start of the file.”. b. Calling the reset() member function using fStr as the calling object but with no argument. c. With calling object fStr call close()then call open( ) with argument “fStr”. d. Only calling the member function open() using fStr as the calling object with the “file.txt” as argument. e. None of the above. You can’t reread lines of a file that have already been read.
The IEEE ____ protocol allows a wireless client to determine the QoS (and security) being used at a different AP before making the transition.
A. 802.11e B. 802.11F C. 802.11q D. 802.11r