A __________ attack is where the source station specifies the route that a packet should take as it crosses the Internet in the hopes that this will bypass security measures that do not analyze the source routing information.
Fill in the blank(s) with the appropriate word(s).
source routing
You might also like to view...
Variables that hold values cannot be used in calculations.
Answer the following statement true (T) or false (F)
Configure switch 1 (sw1), router R1, PC1, PC2, and S1 using the IP addresses provided in Table 1. The IP addresses used in this exercise will all be configured as part of a 192.168.5.0 network.
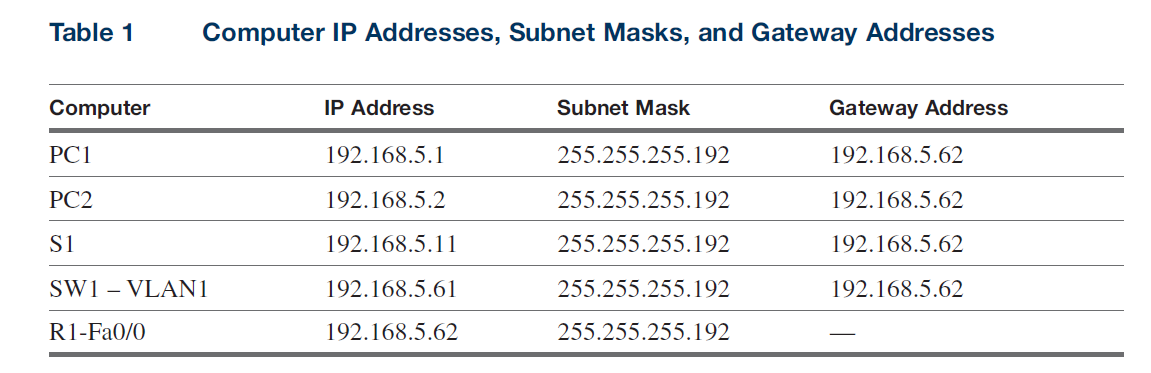
1. Your first task is to configure the switch SW1, the Router R1, the computers PC1 and PC2, and the switch S1 for the network provided in Figure 1. Use the IP addresses provided in Table 1.
2. After you have completed configuring the interfaces, verify that you have connectivity with all interfaces. List the commands used to verify network connectivity. Correct problems as needed.
3. Check whether port security has been enabled on the switch port connected to server S1 by using the show port-security interface Gi0/1 command. Record the status of the port security configuration on the interface based on the first line of output.
4. Configure port security using three commands: one command to make the port a statically configured access port, one command to enable port security, and one command to define the allowed MAC address, namely, S1’s MAC address of 0200.AAAA.AAAA. Record the three commands you used on the lines below.
5. Move back to enable mode and repeat the comman
The flowchart shape for a binary decision is a(n) ________
Fill in the blank(s) with correct word
________ is a major concern for companies that outsource their business applications to ASPs.
(a) Having to maintain a very large IT department. (b) Security. (c) The quantity of time spent on application development. (d) A lack of competition among ASP developers.