__________ implements a security policy that specifies who or what may have access to each specific system resource and the type of access that is permitted in each instance.
A. Audit control B. Resource control
C. System control D. Access control
D. Access control
Computer Science & Information Technology
You might also like to view...
_____________________ is the process of finding a designated target element within a group of items.
a) Sorting b) Searching c) Recursing d) Helping e) none of the above
Computer Science & Information Technology
Files that are next to each other are known as ____ files.
a. contiguous b. continuous c. abutting d. sequential
Computer Science & Information Technology
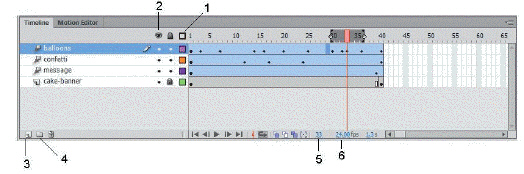 The item marked 6 in the accompanying figure is the Frame Rate indicator.
The item marked 6 in the accompanying figure is the Frame Rate indicator.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Which is NOT true concerning forms?
A) They are used for data entry. B) They can show one or multiple records at a time. C) Every table must have at least one form. D) They can be used to control access to the database.
Computer Science & Information Technology