A programmer has allocated a 32 bit variable to store the results of an operation between two user supplied 4 byte operands. To which of the following types of attack is this application susceptible?
A. XML injection
B. Command injection
C. Integer overflow
D. Header manipulation
Answer: B. Command injection
You might also like to view...
The relation shown in Figure 15.11 lists members of staff (staffName) working in a given ward (wardName) and patients (patientName) allocated to a given ward. There is no relationship between members of staff and patients in each ward. In this example assume that staff name (staffName) uniquely identifies each member of staff and that the patient name (patientName) uniquely identifies each patient.
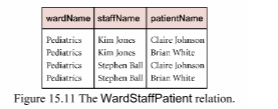
(a) Describe why the relation shown in Figure 15.11 is in BCNF and not in 4NF.
(b) The relation shown in Figure 15.11 is susceptible to update anomalies. Provide
examples of insertion, deletion, and update anomalies.
(c) Describe and illustrate the process of normalizing the relation shown in Figure 15.11 to 4NF.
A(n) ________ is a graphical representation of a file, folder, or drive.
A. directory B. icon C. widget D. path
What are the advantages and disadvantages of using SNMP for WLANs?
What will be an ideal response?
____ are designed to withstand falls from three feet or more onto concrete, extreme temperature ranges, wet conditions, and use while being bounced around over rough terrain in a vehicle.
A. Malleable B. Rugged C. Semirugged D. Flexible