Which of the following is not a symmetric encryption algorithm?
A) DES
B) RSA
C) Blowfish
D) AES
B) RSA
You might also like to view...
Case-based Critical Thinking QuestionsCase 14-2Urma has begun to apply the basic information that you have given her about schemas, and she to understand a schema with and without qualified XML Schema object names.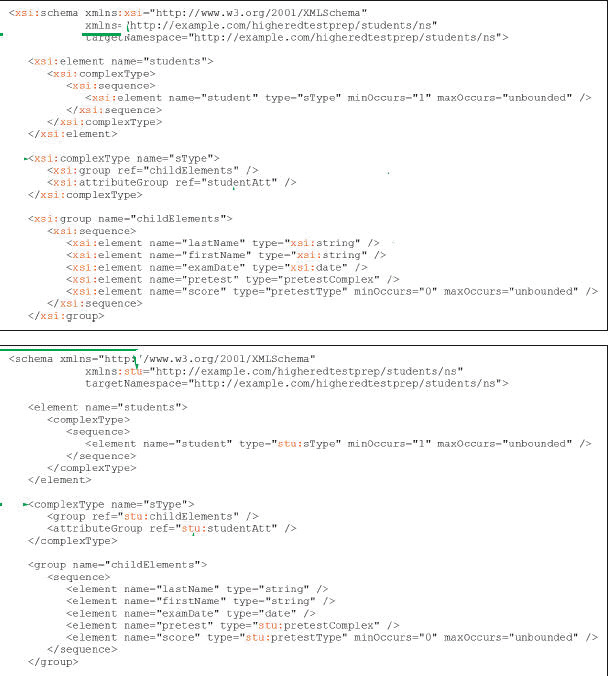 In the example code,
In the example code,
A. xsi B. attributeGroup C. ref D. studentAtt
In the context of Microsoft Excel 2016, which of the following can a Dialog Box Launcher open??
A. ?Table of Contents dialog box B. ?Page Setup dialog box C. ?Header & Footer dialog box D. ?Citations & Bibliography dialog box
In a MenuStrip, placing what character in front of a unique letter allows the user to press Alt and then the given letter to activate the menu choice as an alternative to clicking it with the mouse?
A. % B. $ C. & D. >
Your colleague has not used Visual Basic in a while and so when he encounters a decision point, he sometimes calls out to you over the cubicle wall to get answers to his questions. He wants help remembering which method of passing an argument will give the Sub procedure access to the value of the passed argument without actually referencing the variable declared in the calling procedure. Which of the following do you suggest to him?
A. ByVal B. ByRef C. ByArg D. ByInd