Consider the network topologies shown in Figures 3.7(b–d) of the textbook. Assuming these networks are due to the dynamic nature of the network, estimate the influence stability of the network.
What will be an ideal response?
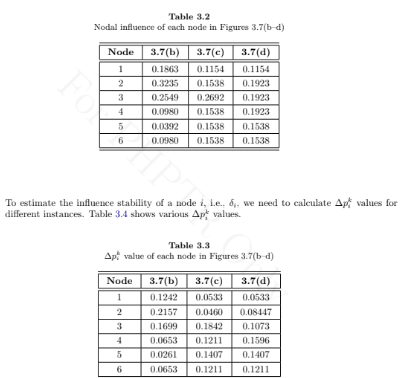
Hence, the influence stability can be estimated as shown in Table 3.4
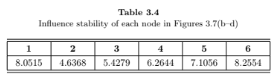
The respective LInE values are as follows:
Figure 3.7(b): 1.6073.
Figure 3.7(c): 2.3517.
Figure 3.7(d): 2.5649.
You might also like to view...
You can specify an access key for an input element by using the ____ attribute.
A. shortcut B. key C. accesskey D. keypress
A visual display of choices from which the user can choose is called a(n) ________
Fill in the blank(s) with correct word
Match the following terms to their meanings:
I. Replicates itself by spreading from computer to computer A. custom scan II. Repair program that closes security holes B. full scan III. A scan that checks only folders/drives that you specify C. patch IV. A scan that checks every file on your hard drive(s) D. quick scan V. A scan that checks areas on your hard drive where E. virus malware programs are likely found
When moving your mouse pointer over a taskbar icon for an open program, a ________ of the file is displayed
A) dialog box B) Key tip C) thumbnail D) shortcut