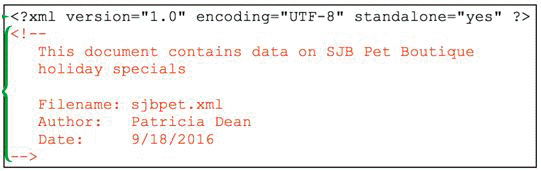
 The orange highlighted item in the accompanying figure is an XML ____________________.
The orange highlighted item in the accompanying figure is an XML ____________________.
Fill in the blank(s) with the appropriate word(s).
comment
You might also like to view...
Which of the following for loops is valid, given the following declaration? String[] names = {"abc", "def", "ghi", "jkl"};
a. for (int i = 0; i < names.length; i++) System.out.println(names[i].length); b. for (int i = 0; i < names.length(); i++) System.out.println(names[i].length); c. for (int i = 0; i < names.length; i++) System.out.println(names[i].length()); d. for (int i = 0; i < names.length(); i++) System.out.println(names[i].length());
In a Token Ring network, a host must __________ before transmitting a message.
a) request the token from another host currently holding the token b) test the medium for any current transmissions c) nothing; the host can transmit immediately d) wait to receive the empty frame
In which subnetting technique can a single address to be subdivided into multiple subnets, in which subnets need not all be the same size?
A. IP gateway B. constant-length subnet masking C. variable-length subnet masking D. IP renumbering
After a company has standardized to a single operating system, not all servers are immune to a well-known OS vulnerability. Which of the following solutions would mitigate this issue?
A. Host based firewall B. Initial baseline configurations C. Discretionary access control D. Patch management system