Which type of attack below is similar to a passive man-in-the-middle attack?
A. replay
B. hijacking
C. denial
D. buffer overflow
Answer: A
Computer Science & Information Technology
You might also like to view...
Would this compile? If not, what change do you need to make so that it will compile?
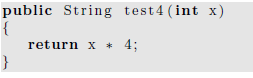
Computer Science & Information Technology
You can use the mathematical operators plus sign (+), minus sign (-), division sign (/), and multiplication sign (*) to build complex formulas
Indicate whether the statement is true or false
Computer Science & Information Technology
Which IP routing protocols are classful?
A) IGRP B) EIGRP C) RIP version 2 D) OSPF E) RIP version 1
Computer Science & Information Technology
What is an adjustment layer and what are its unique advantages?
What will be an ideal response?
Computer Science & Information Technology