Validation of user input data should occur in the business tier of a three-tier architecture.
Answer the following statement true (T) or false (F)
False
You might also like to view...
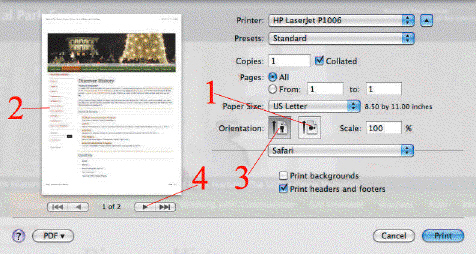 In the accompanying figure of a Safari Print dialog box, Item 3 indicates the ____.
In the accompanying figure of a Safari Print dialog box, Item 3 indicates the ____.
A. Portrait button B. Next page button C. Expand button D. Landscape button
All of the following statements are TRUE about conditional aggregate functions EXCEPT:
A) Elements such as named ranges and cell references should go inside quotes. B) With an aggregate function, a range would still be provided, but the aggregation would only use cells that meet a given criteria. C) Conditional aggregate functions are functions that consolidate or summarize a subset of data that has been filtered based upon one or more criteria. D) The criteria can be on the data that is being aggregated or on associated data.
Which of the following is a situation in which a network with NetBIOS clients would not need to use WINS?
A. It can broadcast across its entire network. B. It is running NetBIOS C. It is part of a larger network with multiple segments. D. It includes Windows 9x systems that are not DNS clients.
Which of the following is not a security principal that can be assigned permissions?
A. computers B. groups C. users D. OU