Sara, the software security engineer, is trying to detect issues that could lead to buffer overflows or memory leaks in the company software. Which of the following would help Sara automate this detection?
A. Input validation
B. Exception handling
C. Fuzzing
D. Code review
Answer: C. Fuzzing
Computer Science & Information Technology
You might also like to view...
To change the time or date, left-click the displayed time and select Adjust Date/Time.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Create a sequence diagram that models the on-site service request mentioned in Task 1.
What will be an ideal response?
Computer Science & Information Technology
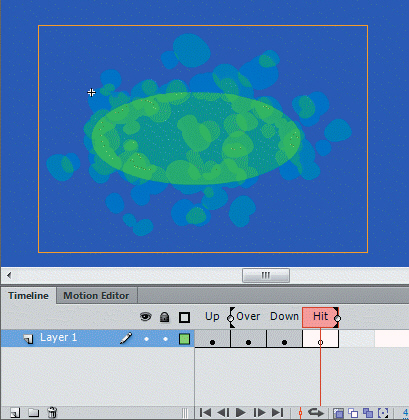 The items circled in the accompanying figure are the frames that have been selected for ____.
The items circled in the accompanying figure are the frames that have been selected for ____.
A. cataloguing B. content previewing C. onion skinning D. concatenation
Computer Science & Information Technology
To enable tracked changes, press ____ on the keyboard.
A. CTRL+SHIFT+E B. CTRL+ E C. CTRL+ T D. CTRL+SHIFT+T
Computer Science & Information Technology