Security testers can use Hping to bypass filtering devices.
a. true
b. false
Answer: a. true
You might also like to view...
The ____ tab menu provides options to change the appearance of the chart labels, data markers, and dimensions.
A. CHARD TOOLS B. GRAPH TOOLS C. IMAGE TOOLS D. GRAPHIC TOOLS
The Access Options button is located in the ________ menu
Fill in the blank(s) with correct word
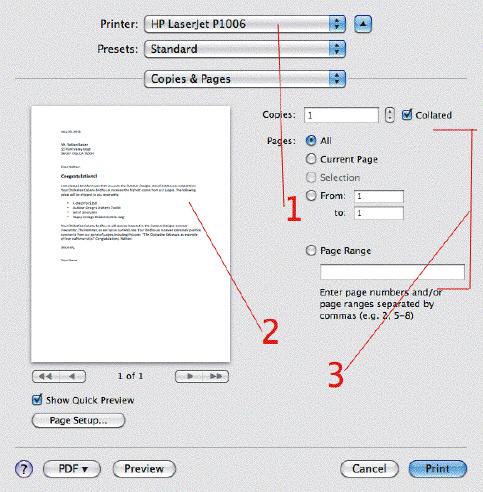 In the accompanying figure, Item 3 points to the ____ options.
In the accompanying figure, Item 3 points to the ____ options.
A. Page range B. Page setup C. Print preview D. Print gallery
Match each term with a statement below.
A. The data components of a class that belong to every instantiated object B. A program or class that instantiates objects of another prewritten class C. The process of acquiring the traits of one's predecessors D. Describes a group or collection of objects with common attributes E. The concept that other classes should not alter an object's attributes-only the methods of an object's own class should have that privilege F. The set of all the values or contents of a class object's instance variables G. Simple numbers and characters H. The characteristics that define an object as part of a class I. The process of combining all of an object's attributes and methods into a single package J. An instance of a class