The performance of a computer can be expressed as the time taken to execute a task. That time is given by:
Time = cycles/instruction × seconds/cycle × instructions/task
Many factors affect the design of a processor; for example, technology, ISA, the compiler, pipelining, superscalar technology. Discuss how these factors affect the above equation.
Cycles per instruction, CPI, is an indication of how many clock cycles are required per instruction. Although this is not a metric that should be used to compare or benchmark computers, reducing the number of cycles per instruction is generally a good thing; for example, by means of pipelining, or by branch prediction. All forms of ILP reduce CPI.
Seconds/cycle is the time per clock cycle. Again, not a good metric, but the faster the clock the greater the speed (in general). Of course, this applies to a given system; that is, increasing the clock rate of a system will usually make it run faster. You can’t compare systems that have different structures on the basis of clock rate.
The time per clock cycle is determined by both the circuit (number of gate delays in series) and the semiconductor technology used to fabricate the circuit. Instructions/task is an indicator of how big the program is (i.e., the number of machine?level instructions). CISC programs used to be smaller than RISC programs because CISC instructions did more work per instruction than RISC instructions (for example, the 68020’s bit field operations). Today, this statement is less true. However, computers like the ARM processor family have attempted to increase the work per instruction by incorporating predicated execution and by including a shift in all data processing operations.
You might also like to view...
Verify Local Connectivity and Test Access Control List
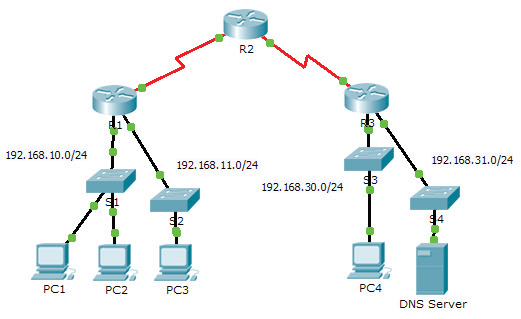
In this activity, you will observe how an access control list (ACL) can be used to prevent a ping from
reaching hosts on remote networks. After removing the ACL from the configuration, the pings will be
successful.
Which protocol does EIGRP use to exchange update messages?
A) RTP B) TCP C) UDP D) RCTP
A query that adds, updates, or deletes data in a database.
What will be an ideal response?
To move the InfoSec discipline forward, organizations should take all of the following steps EXCEPT:
A. form a committee and approve suggestions from the CISO B. learn more about the requirements and qualifications needed C. learn more about budgetary and personnel needs D. grant the InfoSec function needed influence and prestige