Which of the following security evaluation criteria was developed jointly by NIST and NSA?
A. The Federal Criteria for Information Technology Security
B. The Trusted Computer System Evaluation Criteria
C. The Information Technology Security Evaluation Criteria
D. The Common Criteria
Answer: A
Explanation: The Federal Criteria for Information Technology Security (FC) was developed by NIST and NSA to replace TCSEC and introduced the concept of a protection profile (PP).
You might also like to view...
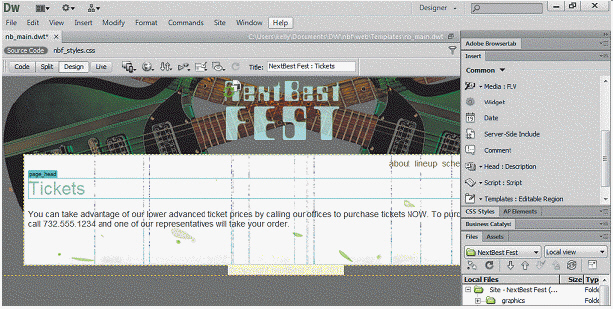 In a file like the kind shown in the Document window in the accompanying figure, noneditable regions are the only regions that can contain unique page content.
In a file like the kind shown in the Document window in the accompanying figure, noneditable regions are the only regions that can contain unique page content.
Answer the following statement true (T) or false (F)
(Removing break and continue) A criticism of the break and continue statements is that each is unstructured. These statements can always be replaced by structured statements. Describe in general how you’d remove any break statement from a loop in a program and replace it with some structured equivalent. [Hint: The break statement leaves a loop from within the body of the loop. Another way to leave is by failing the loop-continuation test. Consider using in the loop-continua- tion test a second test that indicates “early exit because of a ‘break’ condition.”] Use the technique you developed here to remove the break statement from the program of Fig. 4.11.
What will be an ideal response?
Anti-aliasing manipulates the color of edge pixels in a selection to create a visual transition between the selected object and the background.
Answer the following statement true (T) or false (F)
When working with contacts in any view, you can ____________________ the contacts to display them in a different order.
Fill in the blank(s) with the appropriate word(s).