Discuss the situations where NFC security using encryption is acceptable and unacceptable.
What will be an ideal response?
While NFC contains basic encryption, the technology relies on the short distances (<5 cm) and quick communications (hard to target with a man-in-the-middle attack) to provide security. These are acceptable when using NFC for simple data transfers, but are unacceptable for monetary transfers, because bad actors may gain access to personal information.
You might also like to view...
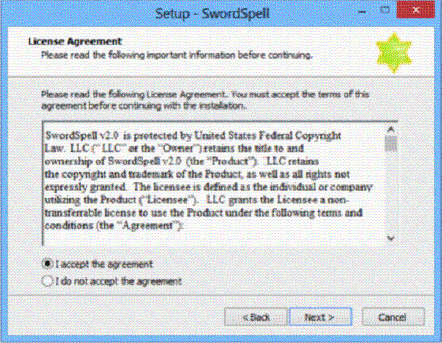 The accompanying figure shows a(n) _____ agreement.
The accompanying figure shows a(n) _____ agreement.
A. EULA B. network license agreement C. single-user agreement D. none of the above
Write a statement that will sets the flag valid data to false when both of the following conditions are true. Assume that valid data has been initialized as true
• large_data_set is true • count is greater than 100 Hint: Build an expression that evaluates to true for the conditions given. Temporarily place a NOT operator in front of it to make the expression false for the given conditions.
Which HTML tag does not require a corresponding closing tag??
A. ?
B. ?
C. ?
D. ?
A ____ Exception occurs when the user enters data that a statement cannot process properly.
A. Style B. Substance C. Format D. Setting