In order to be considered strong today, a symmetric encryption key must be at least ________ bits long.
6
8
100
1,000
Answer: 8
You might also like to view...
Which of the following is not allowed?
a. Objects of abstract classes. b. Multiple pure virtual functions in a single abstract class. c. References to abstract classes. d. Arrays of pointers to abstract classes.
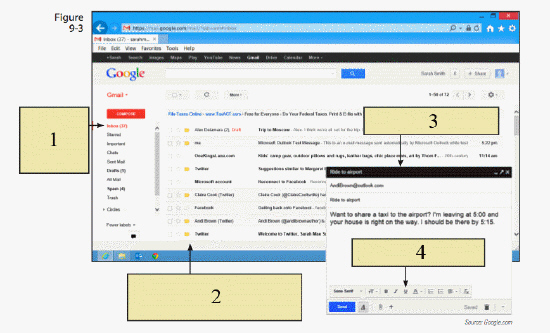 In the figure above, item 1 is pointing to ____.
In the figure above, item 1 is pointing to ____.
A. a copy of the original message and waits for you to add the forwarding address B. a new, blank e-mail and waits for you to add the address and text C. the Inbox and other folders of incoming and outgoing mail D. the e-mail and moves it to the Deleted folder
Mail ________ is the process of combining text from a main document with a data source
Fill in the blank(s) with correct word
In an effort to reduce recovery time during hardware failures, a server administrator needs to implement a backup method that will allow for complete OS and service/application recovery as long as compatible hardware is available. Which of the following backup types meets this requirement?
A. Incremental B. Bare metal C. Snapshot D. Full