Write a simple function template for predicate function isEqualTo that compares its two arguments of the same type with the equality operator (==) and returns true if they are equal and false otherwise. Use this function template in a program that calls isEqualTo only with a variety of fundamental types. Now write a separate version of the program that calls isEqualTo with a user-defined class type, but does not overload the equality operator. What happens when you attempt to run this program? Now overload the equality operator (with the operator function) operator==. Now what happens when you attempt to run this program?
What will be an ideal response?
If the user-defined class does not overload the equality operator (i.e., comment out lines 30–33 in the solution below), the compiler would report an error indicating that the class does not define this operator or a conversion to a type acceptable to the predefined operator. Once the class overloads the equality operator, the program should run fine.
You might also like to view...
Which of following is not a specific criteria for project selection?
A) appropriate timing of project commitment B) practical in terms of resources for the analyst and organization C) backing from programmers D) worthwhile project compared with other ways the organization could invest resources E) possibility of improving attainment of organizational goals
Which is not an advantage of modular programming?
A) Modules make it easier to see the whole program code. B) Tracing an error in a module is less complicated. C) Modules are easier to maintain. D) Modules are easier to grasp.
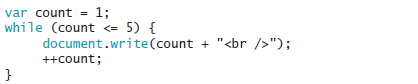 The code shown in the accompanying figure prints the numbers 0 through 4.
The code shown in the accompanying figure prints the numbers 0 through 4.
Answer the following statement true (T) or false (F)
________ means responding to risk by not taking a risky action.
A. Risk reduction B. Risk transference C. Risk acceptance D. Risk avoidance