In which of the following scenarios is PKI LEAST hardened?
A. The CRL is posted to a publicly accessible location.
B. The recorded time offsets are developed with symmetric keys.
C. A malicious CA certificate is loaded on all the clients.
D. All public keys are accessed by an unauthorized user.
Ans: C. A malicious CA certificate is loaded on all the clients.
You might also like to view...
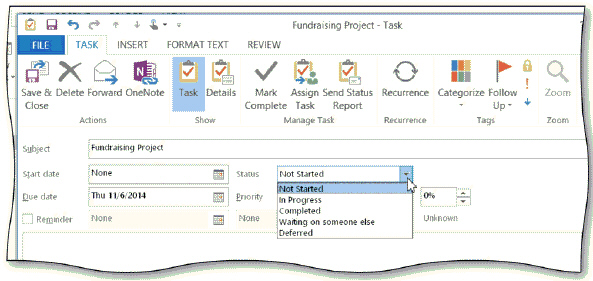 Tap or click the Options box arrow to display the status options, as shown in the accompanying figure.
Tap or click the Options box arrow to display the status options, as shown in the accompanying figure.
Answer the following statement true (T) or false (F)
What will happen if you type man man in Linux?
What will be an ideal response?
Define each of the following terms:
a) Web-based training b) name-your-price model c) shopping cart d) reverse auction e) redundancy f) high-availability computing g) merchant server
________ is a keyboard shortcut for bolding text
A) Ctrl + B B) Shift + B C) Ctrl + D D) Ctrl + I