____________________ risk is the amount of risk left over after countermeasures are implemented.
Fill in the blank(s) with the appropriate word(s).
Residual
Computer Science & Information Technology
You might also like to view...
A base element is one that:
A) was initially keyed into the system. B) does not change over a period of time. C) is used within one and only one subsystem. D) is the result of a calculation or some other logic.
Computer Science & Information Technology
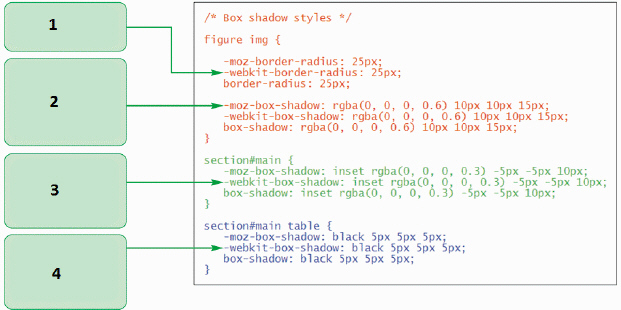 In the accompanying figure, which part adds a semi-transparent black shadow to the lower-right corner of the figure with a blur radius of 15 pixels?
In the accompanying figure, which part adds a semi-transparent black shadow to the lower-right corner of the figure with a blur radius of 15 pixels?
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
Compare TACACS+ and RADIUS with regard to strength of security.
What will be an ideal response?
Computer Science & Information Technology
A DNS amplification attack floods an unsuspecting victim by redirecting valid responses to it.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology