A security technician is concerned there4 is not enough security staff available the web servers and database server located in the DMZ around the clock. Which of the following technologies, when deployed, would provide the BEST round the clock automated protection?
A. HIPS & SIEM
B. NIPS & HIDS
C. HIDS& SIEM
D. NIPS&HIPS
Answer: B. NIPS & HIDS
Computer Science & Information Technology
You might also like to view...
A function that is associated with an individual object is called __________.
a. a static function b. a class function c. an object function d. an instance function
Computer Science & Information Technology
Which of the following domains is used by for-profit businesses?
A) .com B) .edu C) .mil D) .net E) .org
Computer Science & Information Technology
An applet has no constructor or main() method.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
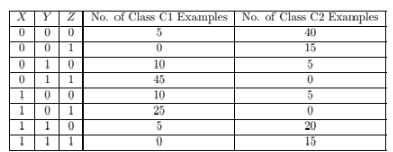
Compute a two-level decision tree using the greedy approach described in this chapter. Use the classification error rate as the criterion for splitting. What is the overall error rate of the induced tree?
Consider the following set of training examples.
Computer Science & Information Technology